“Key” for Secure Data Transmission

“Secure” the most used word in communication world. Most of our Private Office Instant Messenger enterprise customer’s prime question “Is Our chat messages are encrypted ?”. Let’s see the methods available in cryptography and the solutions used in many applications.
Symmetric Key Encryption:
In Symmetric Encryption, a single key is used for both encrypting & decrypting the message. To transform a message from one computer to other, both computers will have a same shared key. The sender will encrypt the data using that key and it is sent over the network to the other computer, where the encrypted packets will be decrypted using the same key.
Asymmetric Key (or Public Key) Encryption:
In Asymmetric Encryption, Pair of keys is used – Public & Private. The Sender will have a Public & Private key pair and the receiver will have a different Public & Private Key pair. Public key is used to encrypt the data & private key is used to decrypt that encrypted data. Both Sender & Receiver share their Public Key, whereas the private key will remain as a secret key & is never exposed. The sender will encrypt the data using receiver’s Public Key and sent over the network to the receiver. The receiver by using private key, can decrypt that data.
When & What to Use :
Symmetric Key is mostly used to transmit the data in network, since it will be faster & simple for communication. BUT to manage the symmetric key between transmitting & receiving nodes Asymmetric key is used. For example, in our Output Messenger Server, all clients are connected under SSL. The same Web Server & Browser logic is followed here.
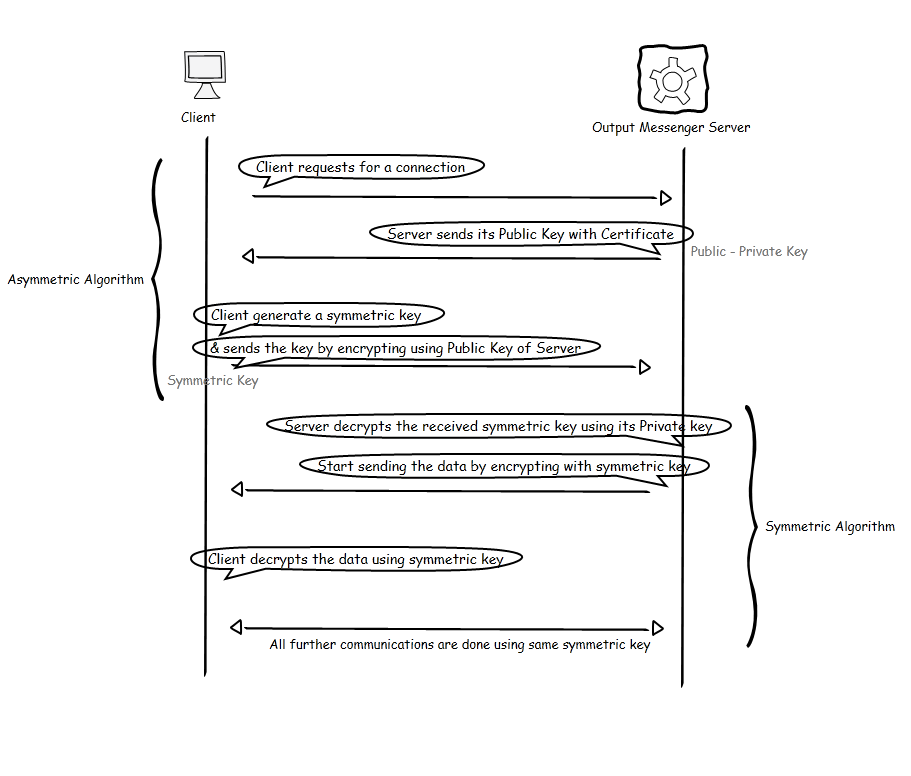
As per the above diagram, Server has Public-Private key pair, sends the public key to the client. Client generates a symmetric key & return to server by encrypting with Public Key. Server decrypts the data using its Private key & stores the symmetric key for that client session. All further communication with the client are encrypted/decrypted using the symmetric key.
Algorithms:
For Asymmetric RSA Algorithm (2048 bit) is the most common used Algorithm
For Symmetric AES Algorithm (256/128 bit) is used in most applications.
- Cassandra – A Linear Scalable Database for Output Messenger - November 20, 2014
- Tirunelveli to Mars - September 25, 2014
- Table Index – Part 2, Multiple Column Index - August 1, 2014
